Registration Magic Version 4.6.0.0 (Multiple XSS Vulnerabilities)
Background
After discovering two new WordPress Plugin vulnerabilities on a recent web application penetration test (which were authenticated and difficult to weaponise) I decided to go in search for some higher ticket WordPress Plugin vulnerabilities in my spare time. I started downloading registration form and forum building plugins, as these are more likely to contain unauthenticated or customer-facing vulnerabilities.
Introducing RegistrationMagic – Custom Registration Forms and User Login version 4.6.0.0 a form building plugin which allows users to create custom login forms, contact forms and other form-based software ideas. However, the vulnerability in the discussion above would need authentication as an administrator to be useful. I had a feeling that a more useful bug could be found in this plugin so started building forms and adding them into my lab.
Read our top tips on securing your WordPres site.
Technical Details
Unauthenticated Stored (XSS) on Contact Form
Here you can see the XSS being injected into the Name field of a contact form generated by Registration Magic.
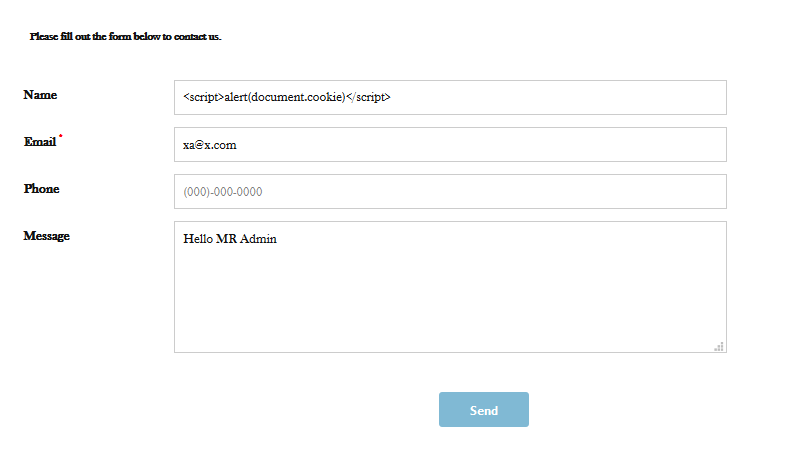
Next, we go to the contact form and select to view the submissions.

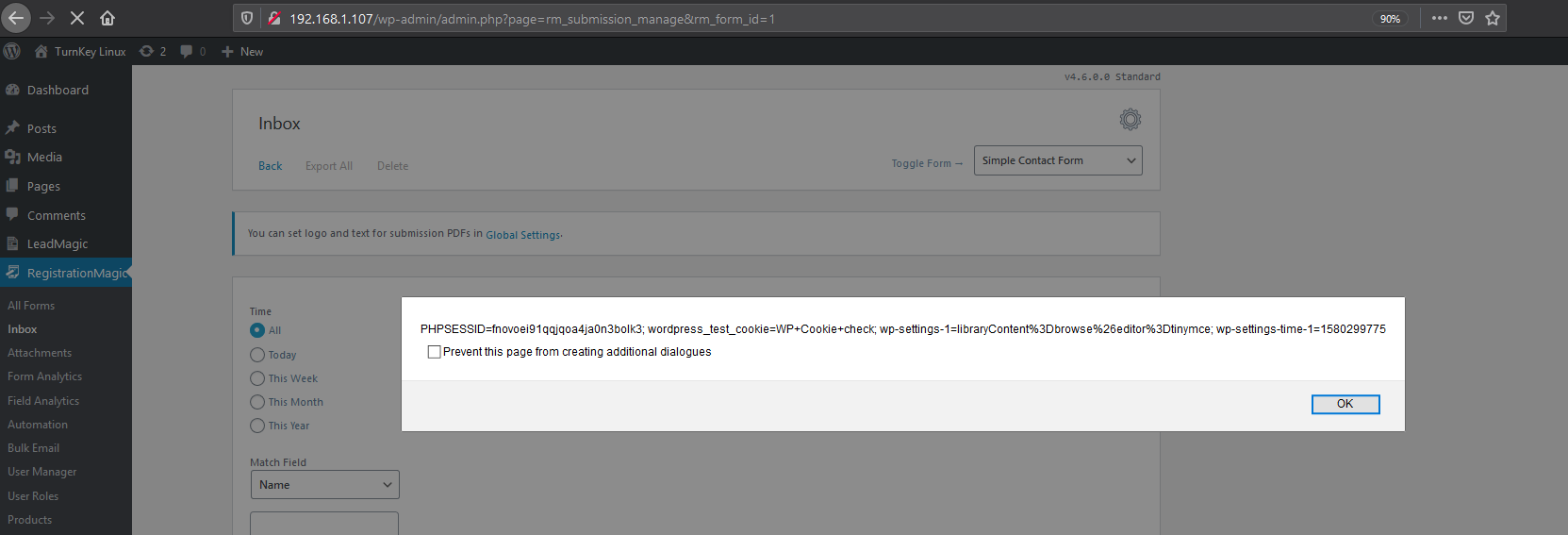
Uh Oh…..so an unauthenticated user can make a submission into one of these generated contact forms and run code inside the administrators’ browser and potentially steal session tokens. Anyone running this plugin could easily lose access to their site.
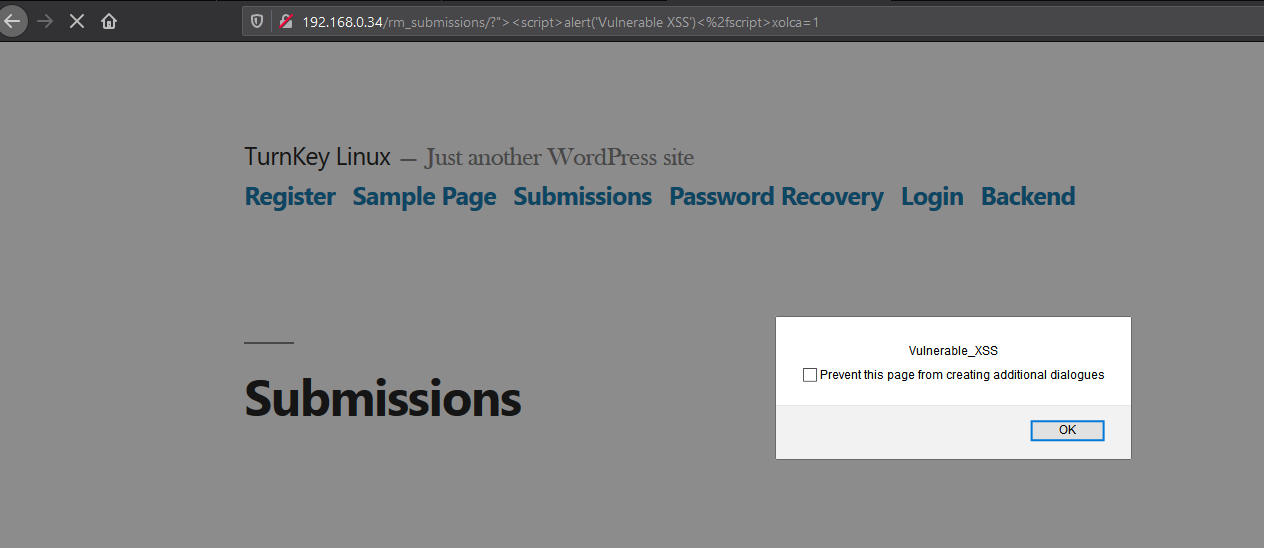
Reflected XSS on Multiple Parameters
Next, we have more XSS vulnerabilities which were discovered during fuzzing.
http://192.168.0.34/rm_submissions/?%22%3E%3Cscript%3Ealert(%27Vulnerable%20XSS%27)%3C%2fscript%3Exolca=1
http://192.168.0.31/wp-admin/admin.php?page=rm_form_sett_manage&rm_form_id=607h4knr%22%3e%3cscript%3ealert(1)%3c%2fscript%3edsukr
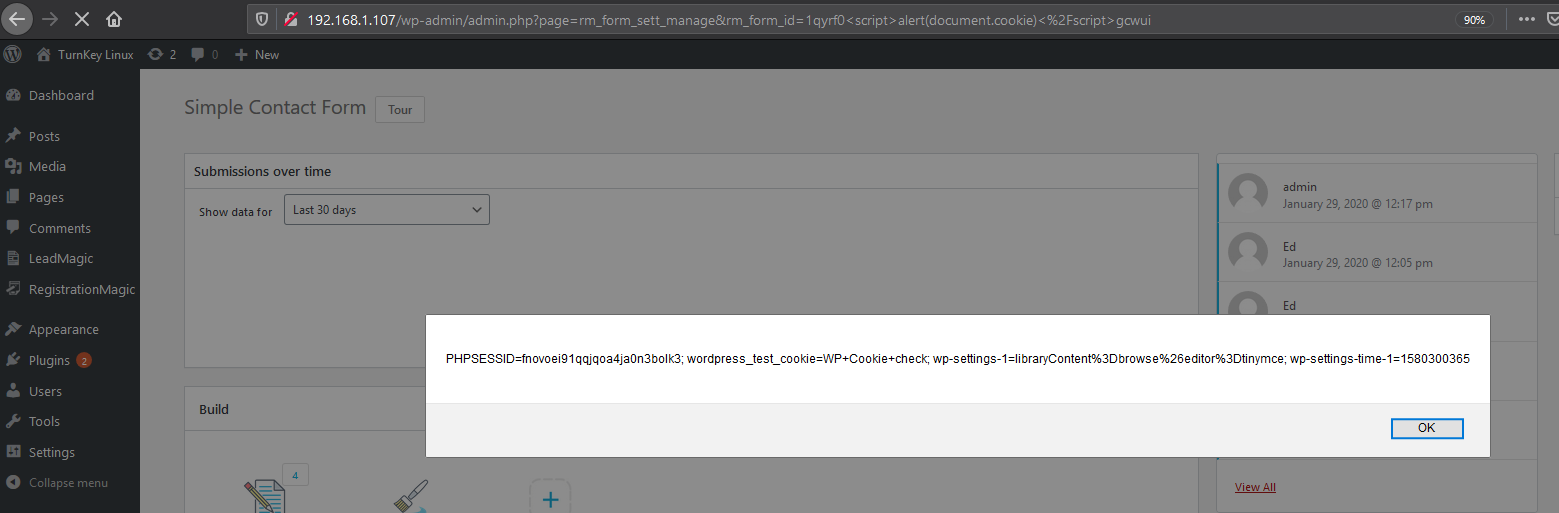
The following parameters were also affected by XSS inside the application.
rm_form_id, form_name,Textarea_, TextBox_
Code Breakdown
Plenty of places in the code parameter values are being taken by the application without proper validation checks. I am going to outline a few examples now.
Here we can see in the comments “take value from various variables and reload pages with those updated”, but there is no validation controls and using an interceptor such as burp we can modify the rm_form_id content in the dropdown.
//Takes value of various status variables (form_id, timeline_range) and reloads page with those parameteres updated.
function rm_refresh_stats(){
var form_id = jQuery('#rm_form_dropdown').val();
var trange = jQuery('#rm_stat_timerange').val();
if(typeof trange == 'undefined')
trange = ;
window.location = '?page=rm_analytics_show_form&rm_form_id=' + form_id + '&rm_tr='+trange;
Here we can see the form_id is being grabbed which is later echo’d into the application browser
$form_id= $_GET['form_id']
Remediation
Update to the latest version of Registration Magic.
