Background
During a web application penetration testing engagement, we discovered our client was using the Chained Quiz Plugin to serve quizzes on the front-end of their site. A quick analysis using WPscan uncovered several historic Chained Quiz Vulnerabilities which had been disclosed in previous versions. As a result of the volume of historic vulnerabilities, we decided to set up a test lab to see if any new vulnerabilities had been introduced into the latest updates. Low and behold we discovered a new unauthenticated Reflected XSS vulnerability, the vulnerability was responsibly disclosed to the plugin developer and an update to the plugin was applied and can be observed here.
Technical Details
The POST parameter ‘total_questions’ fails to sanitize user input. As a result, it is possible to execute client-side JavaScript on a victims PC if the client is tricked into pressing a button containing the malicious request.
An attacker could leverage this vulnerability to steal administrative sessions tokens to a WordPress site or execute code in a victims browser.
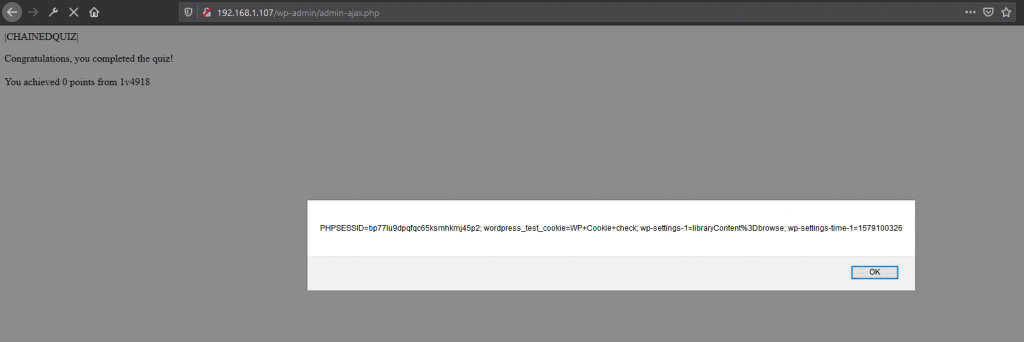
The code in question accepts the ‘total_questions’ parameter without escaping special characters. The vulnerable code can be found in the following php file /models/quiz.php.
$output = str_replace('{{questions}}', $_POST['total_questions'], $output);
Spider Sec probed the Chained Quiz WP Plugin for Vulnerabilities as part of a web application penetration testing engagement.
Remediation
Update to the latest version of this plugin, version 1.1.8.2
